On any given day, you might tap your phone to buy coffee, transfer thousands of dollars to a stranger for a secondhand couch, or split a restaurant bill with friends across three different banking apps. These actions feel instantaneous—almost mundane. Yet beneath each tap and swipe lies DPSIT: the sophisticated fusion of digital payment security and information technology that transforms vulnerable data into protected value.
When your transaction clears in seconds rather than days, when a suspicious charge triggers an immediate alert, when you recognize that a website feels “safe” without knowing exactly why, you are experiencing DPSIT at work. It is not merely a technical requirement or compliance checkbox. It is the invisible architecture that makes modern financial life possible.
The Core Problem DPSIT Solves That Nobody Talks About
Most discussions of payment security focus on preventing theft. This perspective is valid, but it does not tell the whole story. The deeper function of DPSIT addresses something more fundamental: the problem of strangers transacting at scale.
Before digital payments, trust was localized. Your banker was someone you recognized and trusted. Your merchant recognized your face. Transactions occurred between people with a history. Today, global commerce depends on millions of daily exchanges between complete strangers across jurisdictions, currencies, and devices. DPSIT does not just secure data—it manufactures trust where no preexisting relationship exists.
This distinction matters because it reframes how we understand the field. Payment security professionals are not technicians maintaining locks. They are trusted architects designing systems that enable economic cooperation among parties who will never meet.
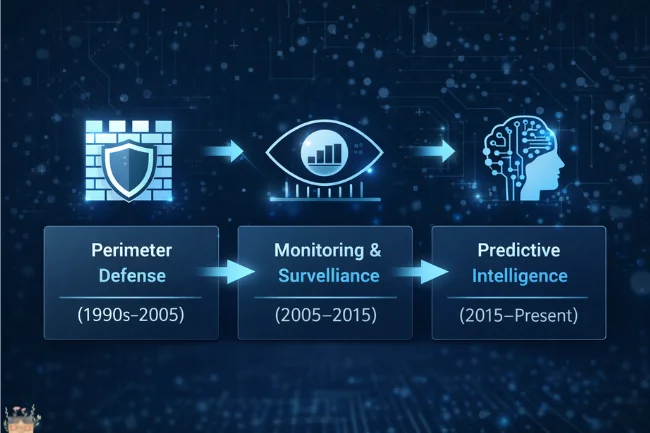
The Evolution of DPSIT: From Perimeter Defense to Predictive Intelligence
Understanding where DPSIT stands today requires recognizing three distinct eras of development.
Phase One: The Fortress Model (1990s–2005)
Early digital payment security operated on perimeter logic. Build a wall around sensitive data. Protect information during transmission. Confirm user credentials at entry points. This approach assumed that external threats were the primary danger and that internal systems, once validated, remained trustworthy. SSL certificates and basic encryption dominated this period.
Phase Two: The Surveillance Model (2005–2015)
As attackers breached perimeters, the industry shifted toward monitoring. Fraud detection systems began analyzing transaction patterns, flagging anomalies, and blocking suspicious activity. This era introduced behavioral analytics and rules-based engines. Security became reactive rather than purely preventive.
Phase Three: The Intelligence Model (2015–Present)
Contemporary DPSIT operates as predictive intelligence. Machine learning models assess risk in milliseconds by evaluating hundreds of variables simultaneously: device fingerprinting, typing cadence, location patterns, merchant relationships, and network reputation. Security no longer halts transactions—it scores them, enabling frictionless experiences where low-risk payments proceed uninterrupted while high-risk attempts receive scrutiny.
This evolution explains why modern DPSIT professionals require fundamentally different skills than their predecessors. Static encryption knowledge no longer suffices. Today’s practitioners must understand statistical modeling, API architectures, regulatory crosscurrents, and user experience psychology.
Deconstructing the DPSIT Stack: What Actually Happens During a Payment
To grasp DPSIT’s complexity, consider what occurs during a routine card-not-present transaction.
Step 1: Device Identification
Before payment data is transmitted, the system evaluates the device. Is this a recognized smartphone with an established history? A new device behaving normally? A known fraudulent endpoint? Modern DPSIT solutions maintain device reputation databases tracking billions of endpoints.
Step 2: Credential Authentication
Multi-factor verification occurs through layered challenges—biometric confirmation, one-time passwords, or behavioral biometrics measuring how the user types or holds the device.
Step 3: Tokenization
Sensitive primary account numbers never travel through the payment ecosystem unprotected. Tokenization substitutes PANs with algorithmically generated surrogates that carry authorization rights without exposing actual credentials. If intercepted, tokens remain worthless outside their specific transaction context.
Step 4: Risk Scoring
Within microseconds, the payment processor evaluates hundreds of risk signals: transaction amount relative to customer history, merchant category, time of day, geographic consistency, and correlation with known fraud patterns. Machine learning models assign confidence scores that determine whether the transaction proceeds automatically or requires step-up authentication.
Step 5: Compliance Verification
Regulatory checks operate simultaneously. Is this transaction subject to sanctions screening? Does it trigger anti-money laundering thresholds? Must it be reported to tax authorities? DPSIT systems encode regulatory requirements directly into payment routing logic.
Step 6: Settlement Authorization
Only after these parallel validations are complete does the transaction receive authorization—an event that consumers experience as a two-second loading screen, unaware of the extensive security infrastructure activated on their behalf.
The Specialized Career Architecture of DPSIT
The competing article correctly notes growing job opportunities but underplays the distinct specialization pathways emerging within the field. DPSIT is not a single career track but an ecosystem of interconnected disciplines.
1- Payment Security Engineers design and maintain the encryption protocols, tokenization systems, and secure APIs that process transactions. Their work occurs at the code level, implementing standards like PCI DSS and EMV 3-D Secure.
2- Fraud Strategy Analysts sit at the intersection of data science and risk management. They analyze historical fraud patterns, tune detection algorithms, and make judgment calls about acceptable trade-offs between security and conversion rates.
3- Digital Compliance Specialists navigate the regulatory labyrinth governing payment systems. They interpret evolving standards—PSD3 in Europe, RBI guidelines in India, state-level privacy laws in the U.S.—and translate legal requirements into operational controls.
4- Payment UX Security Designers represent an emerging role focused on the friction-security paradox. Their mandate: achieve security objectives without degrading user experience. This requires understanding both technical controls and human psychology.
5- Fintech Threat Intelligence Analysts monitor the criminal underground for emerging attack methods targeting payment systems. They track dark web forums, analyze malware samples, and disseminate early warnings to payment processors.
The compensation trajectory reflects this specialization. Senior payment security architects at major financial institutions command salaries comparable to executive leadership in other departments. Mastery within a niche is valued more than surface-level versatility.
DPSIT in Practice: How Organizations Implement Payment Security
Rather than listing companies that “use DPSIT” (a category encompassing virtually every organization processing payments), it is more instructive to examine implementation maturity levels.
Level 1: Compliance-Driven Implementation
Organizations at this stage view DPSIT as a regulatory obligation. They meet minimum PCI DSS requirements, conduct annual assessments, and respond to incidents reactively. Common among small businesses and legacy retailers transitioning to e-commerce.
Level 2: Risk-Management Implementation
These organizations maintain dedicated security teams, proactive monitoring, and formal incident response procedures. They view DPSIT as insurance against financial loss and reputational damage. Typical of mid-market enterprises and established fintechs.
Level 3: Business-Enablement Implementation
Mature organizations treat DPSIT as a competitive advantage. Their security infrastructure enables product innovation—instant payment approvals, cross-border expansions, embedded finance integrations—that competitors cannot match. Characteristic of market-leading payment platforms and digital-first banks.
The distinction matters because career opportunities differ dramatically across maturity levels. Level 1 organizations seek compliance officers. Level 3 organizations seek innovation enablers who understand security as a product feature, not a cost center.
The Vulnerability That Keeps DPSIT Professionals Awake
Industry literature emphasizes external threats—cybercriminals, organized fraud rings, and nation-state actors. The risks are not hypothetical. Yet experienced practitioners worry more about architectural debt.
Payment systems evolve through accretion. New security layers stack atop legacy infrastructure. Authentication requirements are compound. Compliance patches accumulate. Over the years, the system becomes increasingly brittle—not because any component fails individually, but because the interactions between components grow unpredictable.
This weakness often reveals itself in quiet, unexpected ways. A routine software update triggers unexpected fraud flags. A legitimate customer receives repeated authentication challenges and abandons the purchase. A compliance rule written for card transactions does not apply to digital wallets. These incidents do not make headlines, but they erode trust incrementally.
The most valuable DPSIT professionals are not those who understand individual security tools, but those who comprehend system dynamics—how security controls interact, where complexity creates hidden risk, and when simplification serves security better than addition.
DPSIT and Financial Inclusion: An Overlooked Dimension
Standard discussions frame payment security as protection for existing financial participants. This perspective neglects DPSIT’s role in enabling first-time entry into formal financial systems.
In emerging economies, millions of individuals conduct their first digital transaction through government benefit programs or mobile money services. These systems must balance fraud prevention with accessibility. Overly stringent security excludes precisely those populations—elderly, rural, technologically inexperienced—that inclusion initiatives aim to reach.
This creates distinct design challenges. How do you authenticate users without assuming smartphone ownership? How do you detect fraud in populations without established transaction histories? How do you balance consumer protection with proportional regulation?
DPSIT practitioners addressing these questions work at the frontier of financial development. Their technical decisions determine whether previously unbanked populations experience digital finance as empowering or exclusionary.
FAQs About DPSIT Careers and Practice
Is DPSIT primarily a technical field or a business discipline?
Both. Entry-level positions emphasize technical implementation, but senior practitioners spend substantial time on risk quantification, regulatory interpretation, and cross-functional communication. The most effective professionals translate between engineering and business stakeholders.
What certifications carry weight in DPSIT hiring?
Employers value demonstrated competence over credential collection. The Certified Payment Card Industry Security Manager (CPCIP) and Certified Information Systems Security Professional (CISSP) remain relevant. However, practical experience with specific technologies—AWS security services, fraud detection platforms, tokenization vendors—often outweighs generic certifications.
How does DPSIT differ from general cybersecurity?
General cybersecurity protects information assets broadly. DPSIT specifically concerns financial transaction systems, which operate under unique constraints: sub-second latency requirements, complex regulatory oversight, and direct consumer impact. A skilled network security engineer may require six to twelve months to become productive in payment security specifically.
What is the geographic distribution of DPSIT jobs?
While financial centers concentrate employment, remote work has expanded opportunities significantly. Singapore, London, New York, and Bangalore maintain dense DPSIT hiring ecosystems, but distributed teams are increasingly common. Payment processing is inherently global, and security teams reflect this.
How do I transition into DPSIT from adjacent fields?
Successful transitions often leverage domain expertise. Fraud analysts from traditional banking bring risk assessment experience. Software engineers from e-commerce understand transaction systems. Compliance attorneys contribute regulatory knowledge. The field values specialized entry points rather than requiring dedicated academic preparation.
The Horizon: Where DPSIT Moves Next
Three developments will reshape DPSIT over the next five years.
Embedded Finance Security
As financial services integrate into non-financial contexts—ride-sharing apps, retail platforms, social media—security controls must similarly embed. Future DPSIT solutions will operate invisibly within diverse digital environments rather than existing as discrete payment gateways.
Post-Quantum Cryptography
Current encryption standards face eventual obsolescence as quantum computing advances. Migration to quantum-resistant algorithms represents a multi-year infrastructure project comparable to Y2K remediation in scale and complexity. Organizations beginning this planning now will avoid crisis-mode transitions later.
Decentralized Identity Protocols
Traditional authentication relies on centralized credential repositories, which present attractive targets for attackers. Emerging standards enable self-sovereign identity—users controlling their own credentials without institutional storage. Early implementations suggest this model reduces both fraud risk and compliance burden.
Why DPSIT Demands More Than Technical Competence
Return to the problem of strangers transacting at scale. Every digital payment represents a leap of faith—consumer trusting merchant, merchant trusting payment processor, processor trusting issuing bank, all parties trusting technology they do not understand.
DPSIT professionals hold this trust on behalf of everyone else. Their code, their risk models, and their compliance interpretations determine whether economic exchange continues smoothly or fractures under suspicion. The responsibility is not merely technical but social.
This explains why the field attracts individuals motivated by more than salary or job security. Payment security practitioners describe their work in terms of protection, enablement, and participation—ensuring that a grandmother purchasing school supplies online experiences the same safety as a corporate treasury moving millions, that a farmer accessing mobile payments for the first time is not defrauded on their initial transaction, and that innovation outpaces exploitation.
Digital payment security technology is, ultimately, civilization’s infrastructure. It allows individuals with no prior connection to work together confidently. It allows resources to flow toward productive use. It makes the economy legitimate and accountable.
And it requires people who understand that securing a transaction is not the final objective. The final objective is securing the trust that makes transactions possible.
The architecture of modern payment security remains largely invisible to those it protects. The fact that it goes unnoticed is proof of its success. When DPSIT functions correctly, participants experience only seamlessness—the quiet confidence that their money will arrive where intended, their data will remain private, and their trust will prove well placed. For the professionals building and maintaining these systems, no greater validation exists.
Alex Carter is a writer with 10+ years of experience across tech, business, travel, health, and lifestyle. With a keen eye for trends, Alex offers expert insights into emerging technologies, business strategies, wellness, and fashion. His diverse expertise helps readers navigate modern life with practical advice and fresh perspectives.